CAPSTONE PROJECT



Showcasing cybersecurity and IT skills thought Penetration testing and Wireshark analysis
Task #1001 Penetration, testing And vulnerability Assessment
Reconnaissance & scanning
Phase 1 of this gray-box penetration test focuses on reconnaissance and enumeration using Nmap to uncover open ports, services, OS details, and potential vulnerabilities with limited prior knowledge of the target system.
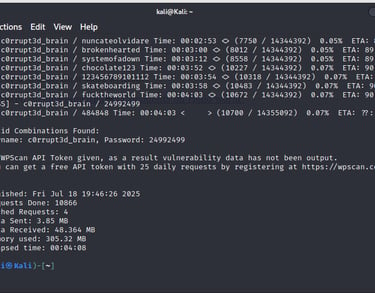
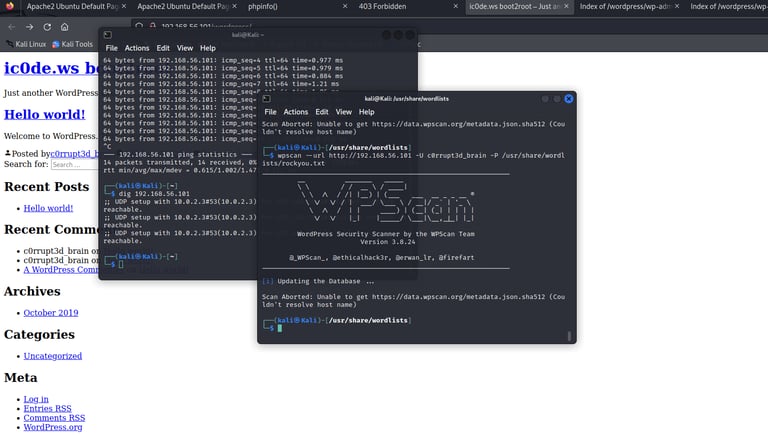
Exploitation Phase
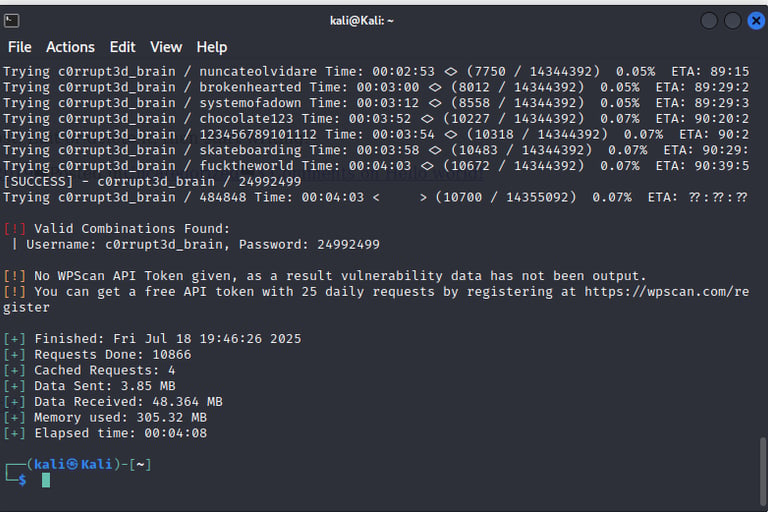
Using known vulnerabilities to gain unauthorized access and escalating privileges using tools such as Nikto, dirb, and Metasploit.
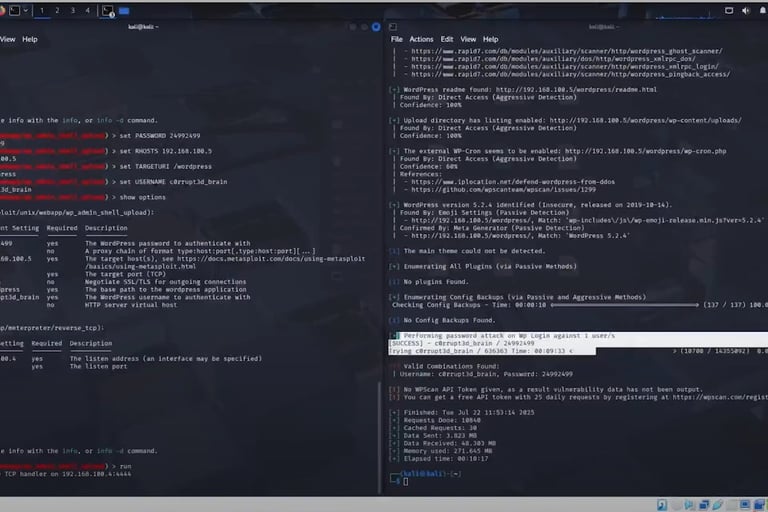
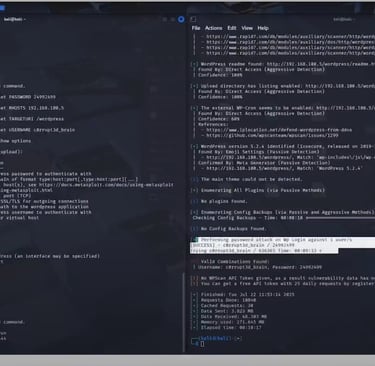
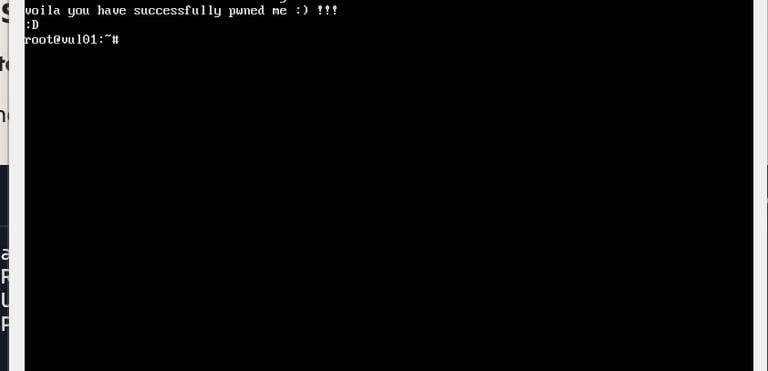
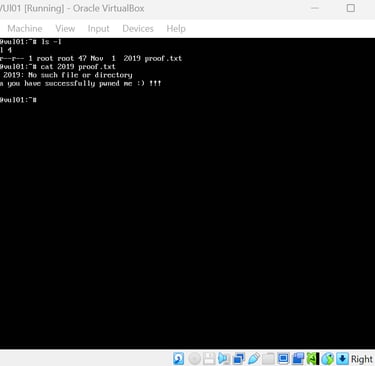
Mitigation recommendations
Apply principle of least privilege
Patch management
Access Controls Audits
Multi-Factor Authentication
Enable lockout policies
Security Awareness and password hygiene


Wireshark analysis task #1002
Packet Analysis Insight: After capturing over 75,000 packets, Wireshark tools revealed a notable pattern—numerous empty IPv4 packets linked to sequential MAC addresses. This suggests ARP scanning or spoofing-based reconnaissance, likely driven by an automated host discovery method using systematic MAC enumeration via ARP requests.
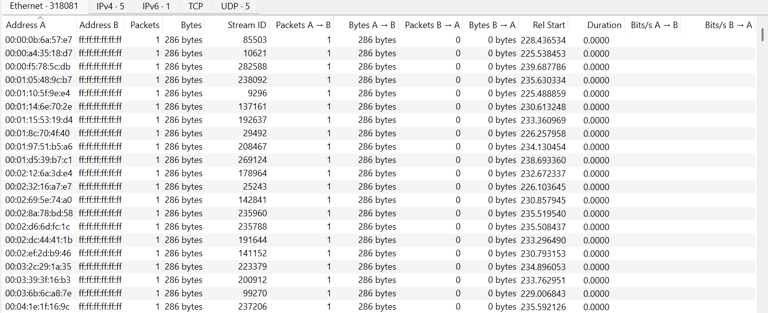
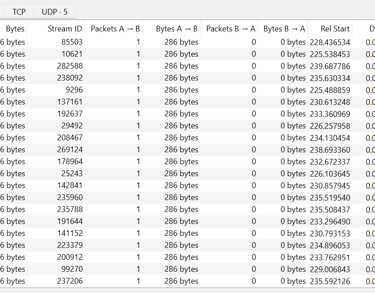
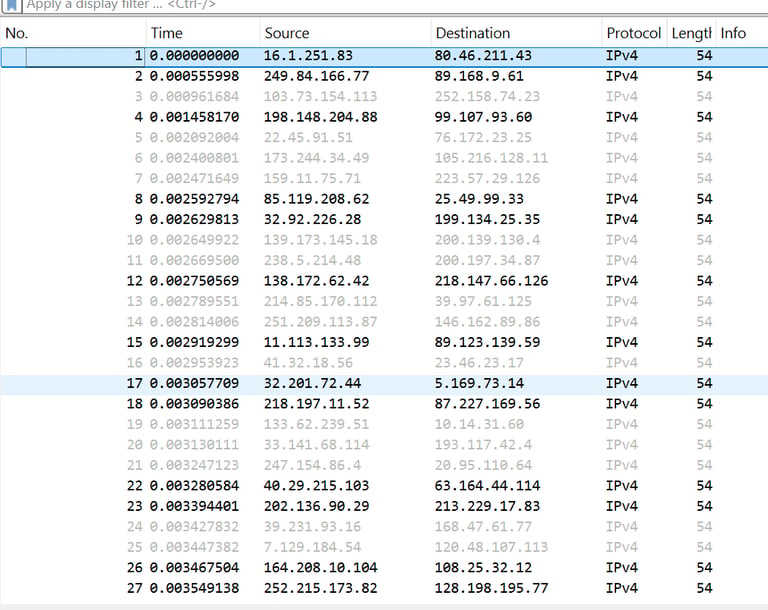
Mitigation Recommendations
Limit ARP exposure
Harden ICMP Behavior
Update/Disable Legacy Protocols
Implement Network Segmentation & Isolation to prevent lateral movement and escalation of privileges
Wireshark analysis task #1003
SYN Flood Behavior Captured repeated TCP SYN packets to port 80 from spoofed external addresses without corresponding ACKs. Pattern indicates attempted SYN flood DoS, tactic wherein the target is overwhelmed with incomplete connection requests, exhausting system resources and degrading service availability targeting web services on 10.2.2.8.
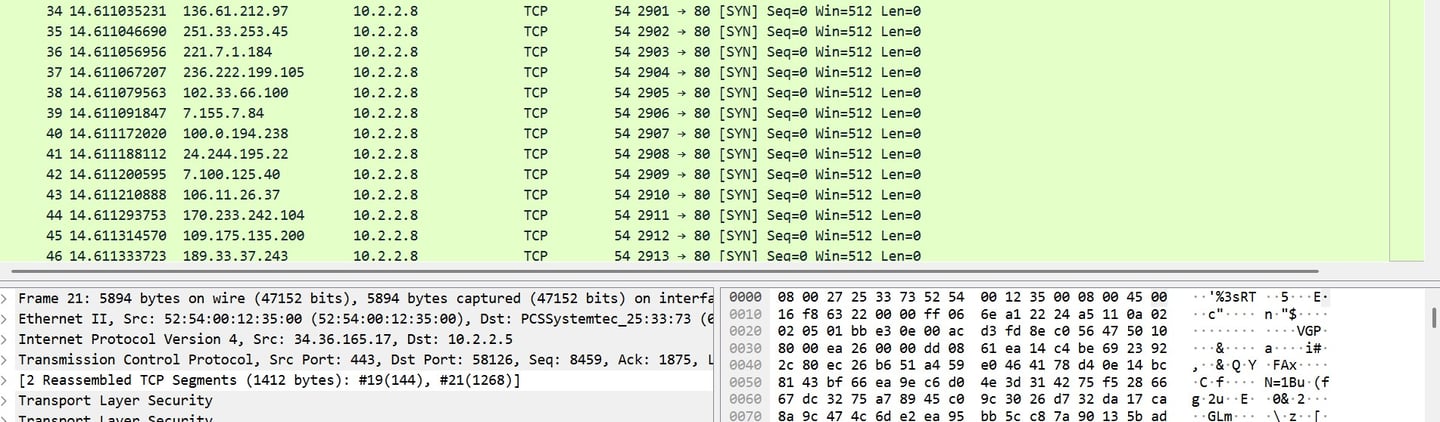
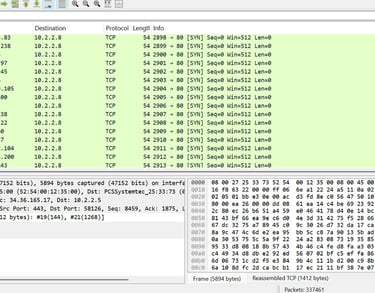
Mitigation recommendations.
Implement SYN rate-limiting and firewall protections to suppress floods attempts
Enhance internal monitoring for TLS handshake anomalies and ARP surges
Evaluate endpoint exposure via DNS-linked advertisements or third-party redirects
Segment hosts with VLAN and isolate vulnerable devices to reduce the attack surface area.


TASK #1004-Wireshark capture analysis
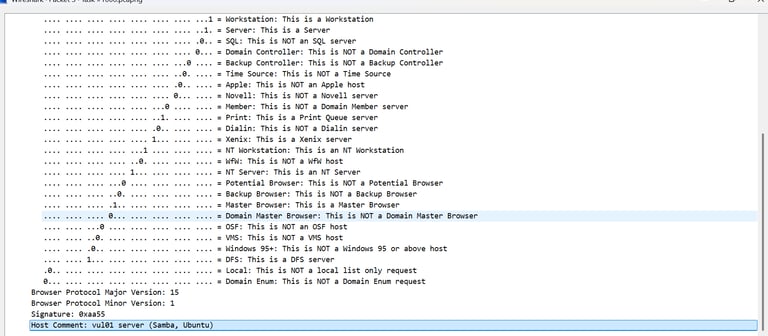
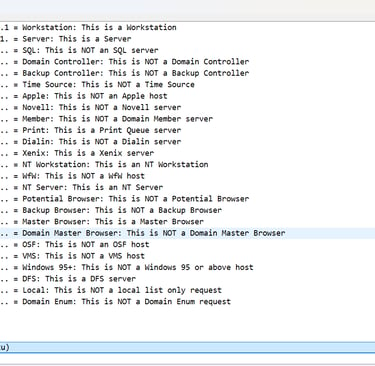
The activity points to possible network misconfiguration with multiple devices acting as routers, potential spoofing from unexpected MAC addresses, and IPv6 router discovery—likely used to map infrastructure and target services
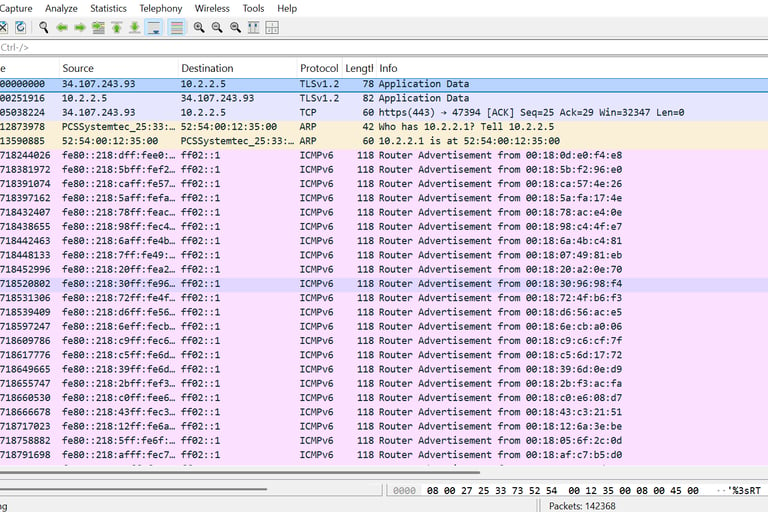
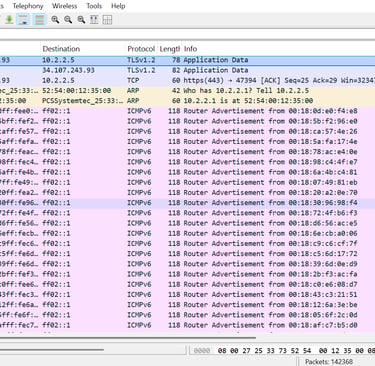
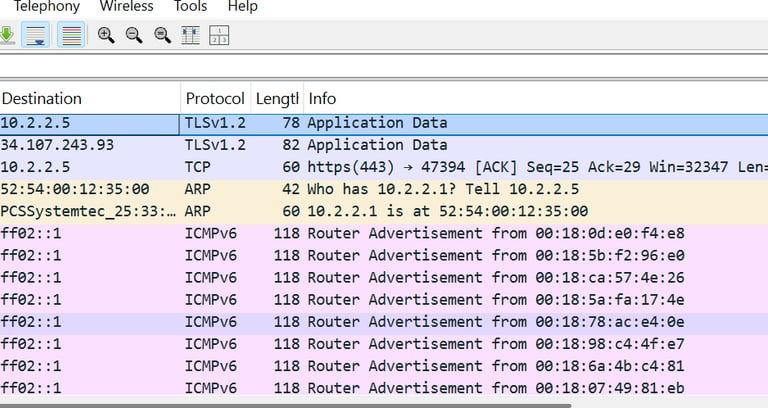
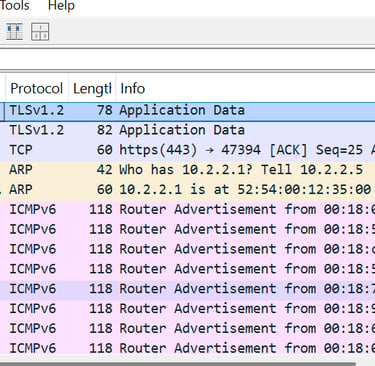
Mitigations Recommendations
Strengthen endpoint defenses with updated antivirus signatures for trojans and rootkits
Harden the network by disabling ICMPv6 broadcasts and blocking known malicious MAC addresses
Implement monitoring with alerts for spoofing activity and spikes in encrypted traffic.

TASK #1005-Wireshark capture analysis
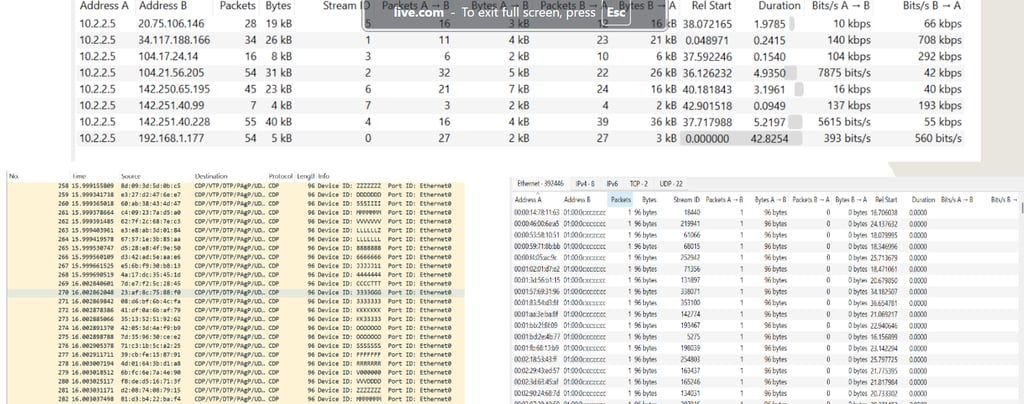
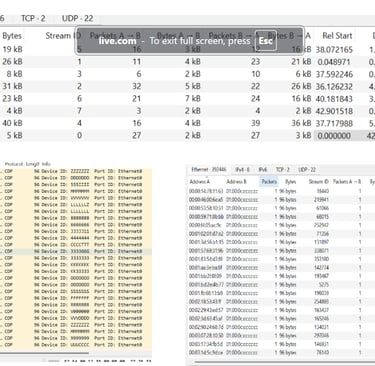
Wireshark analysis revealed aggressive CDP flood-based reconnaissance, MAC spoofing, and SYN probing activity, indicating targeted efforts to map Cisco device metadata. Thousands of CDP broadcasts were sent to a single host with no replies, suggesting passive fingerprinting. A spoofed MAC initiated rapid three-way handshakes with host 10.2.2.5, alongside bursts of CDP packets and filtered SYN probes, raising concerns about data exfiltration during an active scanning phase.
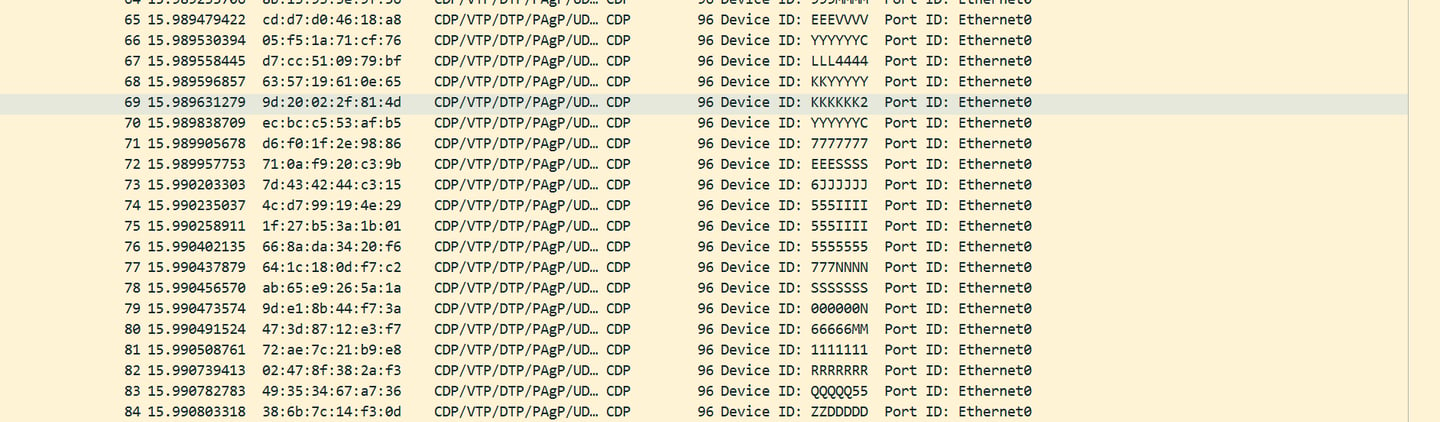
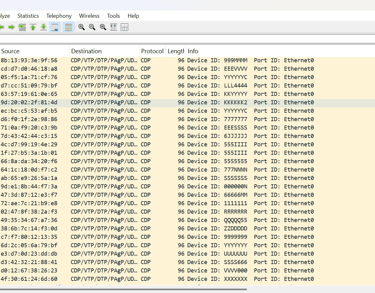
Mitigation Recommendations
Implement Network Access Controls
Protocol filtering
Implement MAC Spoofing Defense
TCP Scan Mitigation
Segmentation
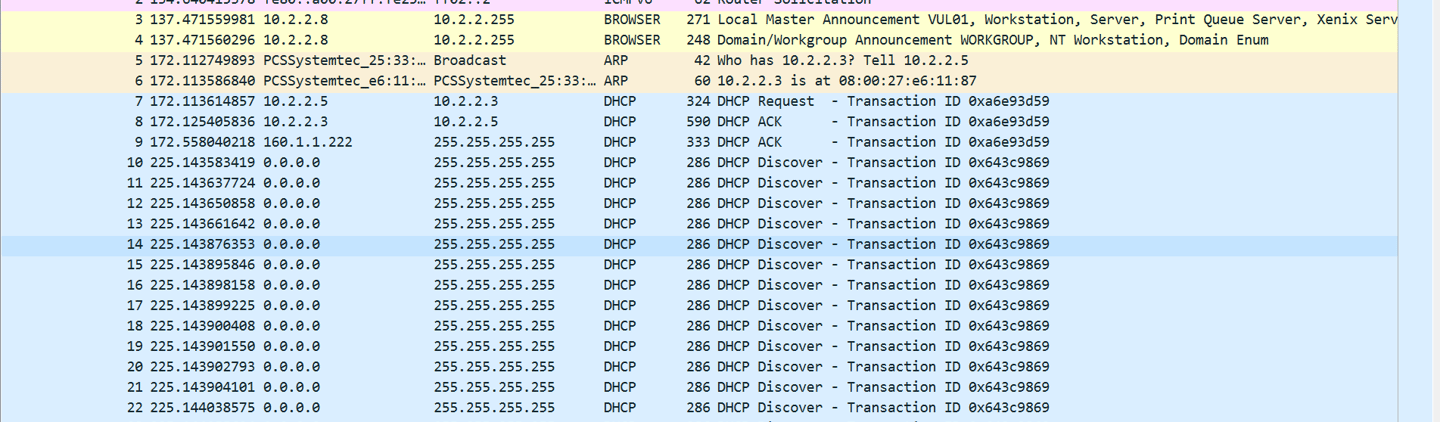
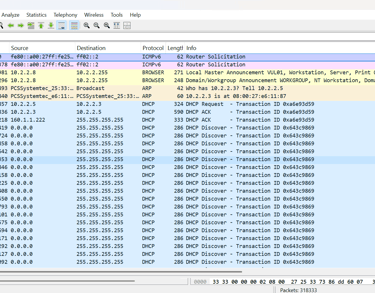
TASK #1006-Wireshark capture analysis
This Wireshark capture reveals a clear DHCP Starvation attack, where the network was flooded with DHCP DISCOVER packets starting around packet 7 and escalating until capture 204,211. This suggests the attacker used automated MAC spoofing, crafting rapid requests from fake identities to exhaust the DHCP server’s IP pool.
Mitigation Recommendations
Implement Network Defense to detect DHCP Snooping, Port Security, VLAN Segmentation.
Implement Network Traffic control
Integrate IDS/IPS to detect Anomalies in Network Behavior
Conduct periodic testing and validation to ensure controls hold under pressure